Public Key Infrastructure Explained!

What is Public Key Infrastructure?
Public Key Infrastructure (PKI) is often described as a set of rules, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption, as a back-end cybersecurity measure.
What is it used for?
PKI is witnessing increasing popularity and is being used in everything from enabling the internet of things (IoT) communication security to enabling digital document signing. PKI, which is based on asymmetric cryptography, is used widely in securing electronic communications for online shopping, banking, emails, as well as communications between users and the websites they connect to, using HTTPS. PKI provides digital identities for people, services, and things, enabling strong authentication, data encryption, and digital signatures. These security mechanisms are used to provide secure access to physical and digital resources; secure communication between people, services, and things; and enable digital signing of documents and transactions.
PKI Key Components
In the center of the PKI infrastructure is a certificate authority, which is a trusted entity that ensures the trustworthiness of the digital certificates. The purpose of the PKI is to reliably tie a public key to a person, service, or object.
Let’s have a look at the typical key components of a PKI:
- Certificate Policy. The certificate policy is the security standard that defines the structure and hierarchy of the PKI infrastructure. It also defines the policies regarding the management of keys, secure storing, and management of keys, revocation, and certificate formats.
- Root Certificate Authority (CA). The Root Certificate Authority is an entity that is the “root of trust” in a PKI implementation and is responsible for authenticating identities in the ecosystem.
- Intermediate CA (Or subordinate CA). The intermediate CA is verified by a root CA for specific operations, as defined by the certificate policy. Digital certificates are typically issued and signed by Intermediate CAs.
- Certificate Database. The certificate database stores certificate records.
- Revocation Services. Revocation services are servers that maintain updated Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) responders. These use CRLs and respond to revocation lookup checks for devices that may not manage CRLs themselves.
- Digital Certificate. The digital certificate is a “digital identity” within a device, and provides secure authentication between devices and servers, allowing them to access services, files or other information, and is typically issued by the sub-CA.
What is a digital certificate?
A digital certificate is a document containing data, such as identifying information, a serial number, and expiration dates. Within the information, we also see the digital signature of the certificate authority that issued the certificate, which provides validity to the certificate, as well as the certificate holder’s public key.
What are the public and private keys?
In cryptography, a key is data that determines the functional output of a cryptographic algorithm. Public and private keys are propagated in pairs that are mathematically linked. These key pairs are used in asymmetric cryptography, also referred to as public-key cryptography. The public key is open for access to everyone, while the private key is only known to the key holder.
The only way to decrypt the data encrypted by a public key is to use the linked private key. When a private key is used to sign a message, we can use the linked public key to verify the signature. By maintaining “asymmetry” via the use of two different keys, asymmetric cryptography received its definition. For comparison, in symmetric cryptography, the same key is used for both encryption and decryption.
To recap, in PKI, a pair of keys is created: a private key and a public key. The private key is not shared and is used only by the signer to electronically sign documents. The public key can be shared and is used to validate that signature. Despite the fact that you can easily encrypt messages without PKI, you cannot easily verify the identity of the other party. At the end of the day, a PKI infrastructure aids in verifying the identity of whom you are communicating with.
What makes up a digital identity?
A digital certificate, which is publicly available and includes both public and digital signature. In combination, this works as a digital passport: it can be used to affirm the identity of service, person, or even a thing.
How does PKI facilitate authentication?
For example, when a user tries to authenticate their identity to a server, the server generates random data and sends it back to the user. The user then encrypts the data with their private key and sends it back to the server. The server decrypts the data with the public key in the user’s digital certificate, and if the decrypted data is the same as the sent data, then the server knows that the user is who they claim to be.
How does PKI facilitate digital signing?
Firstly, we need to calculate the hash value of the data being signed. The hash value is produced with an algorithm and the output may be described as a digital fingerprint of the data’s contents. Secondly, the hash value is signed with the user’s private key, and the hash value’s signature is added to the document or transaction, creating the signature. Thirdly, anyone can validate the signature using the public key and calculate the hash value of the document. If the two results are identical, then we can be sure that the signature and the integrity of data is verified.
How does PKI facilitate encryption and decryption of data?
When large amounts of data need to be encrypted and decrypted, the solution is the use of symmetric cryptography, since asymmetric cryptography is too slow. Since in symmetric cryptography the same key is used for both encryption and decryption, the key first has to be shared between the two communicating parties. Usually, one of the parties generates the key and sends it to the other party using asymmetric cryptography, which is of course enabled by the PKI.
How Does Public Key Infrastructure Work?
Asymmetric authentication is often structured in a hierarchy of CAs that may sign and issue digital certificates or credentials. See below for an example of a PKI hierarchy:
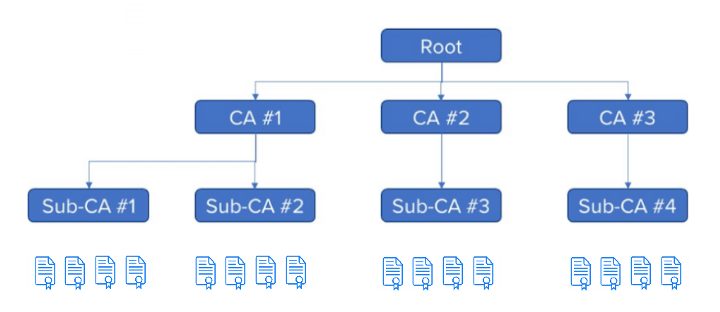
Each CA provides authority to sub-CAs, as to sign digital certificates for devices. The digital certificates at the bottom are transmitted by end devices and are authorized by the sub-CA above them, that generated and signed them. Generally, these are called device certificates. The sub-CAs that generate the device certificates, carry their own certificate, authorized by the digital signature of CA above them, and so on. PKI eventually ends at the root, the foundation on which this particular PKI ecosystem domain is constructed.
By arranging PKI ecosystems in hierarchies, we allow for selective levels of revocation or access denial, in the case that a leak or compromise of a private key in the ecosystem has occurred, as shown below:
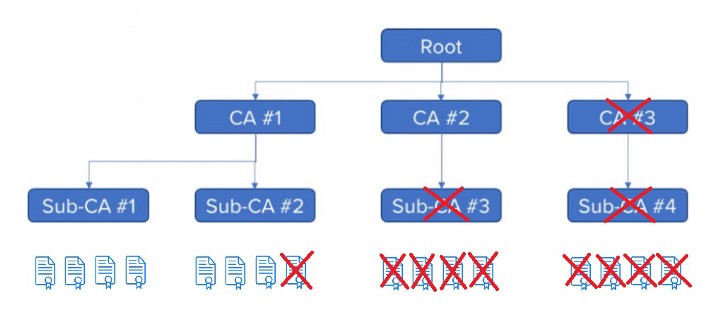
As the above figure shows, everyone can revoke the certificate of any element within PKI from the device up to a high-level CA, always depending on the nature of the security compromise. However, it also needs to be noted that if you revoke a certificate, you also revoke anything that is below the element in the hierarchy.
Moreover, this illustrates why PKI implementations are set up in tree-like hierarchies: this design allows for the ecosystem owner to perform selective damage control in the event of a compromise. This is why it is not a good idea to issue any device certificates off the root CA, as it limits flexibility. In this case, if something goes wrong, we may need to invalidate and revoke the entire PKI and all deployed devices in the field. For this reason, device certificates are almost always issued by sub-CAs below the root.
Lastly, the largest benefit is that with a single sub-CA generating potentially millions of device certificates, we can authenticate millions of devices with one sub-CA public key, making key management far more scalable and manageable than other options.
What does EU regulation say?
According to eIDAS: Electronic signature means data in electronic form which is attached to or logically associated with other data in electronic form and which is used by the signatory to sign. This could be just an image but also a digital signature. E-signature is used as an umbrella term; i.e. digital signatures are e-signatures.
Furthermore, eIDAS concludes that an advanced electronic signature shall meet the following requirements:
- It is uniquely linked to the signatory;
- It is capable of identifying the signatory;
- It is created using electronic signature creation data that the signatory can, with a high level of confidence, use under his sole control; and
- It is linked to the data signed therewith in such a way that any subsequent change in the data is detectable.
If your brand is ready to take the step into web 3.0 and NFT marketing, to optimize engagement with your audience in innovative ways, then click the button below to get your Free Trial, a limited number of Free NFTs, and a Free Consultation call from our team!
For more info, contact Block.co directly or email at enquiries@block.co.
Tel +357 70007828
Get the latest from Block.co, like and follow us on social media: